Phishing attacks remain a pervasive online threat, aiming to deceive users and compromise their sensitive information. In this article we will explore practical tips to recognize, avoid, and counter phishing attacks, empowering you to navigate the web securely.
Phishing is one of the most common types of social engineering attacks. It's an attempt to trick a victim into revealing critical information, usually via email. Most likely, you've seen emails that start with an offer or a lottery saying you just won a million dollars or even the government who returns your tax money.
Recognizing Red Flags:
Sometimes phishing emails are easy to spot and are automatically filtered by our email's spam settings. Let's look at an example.

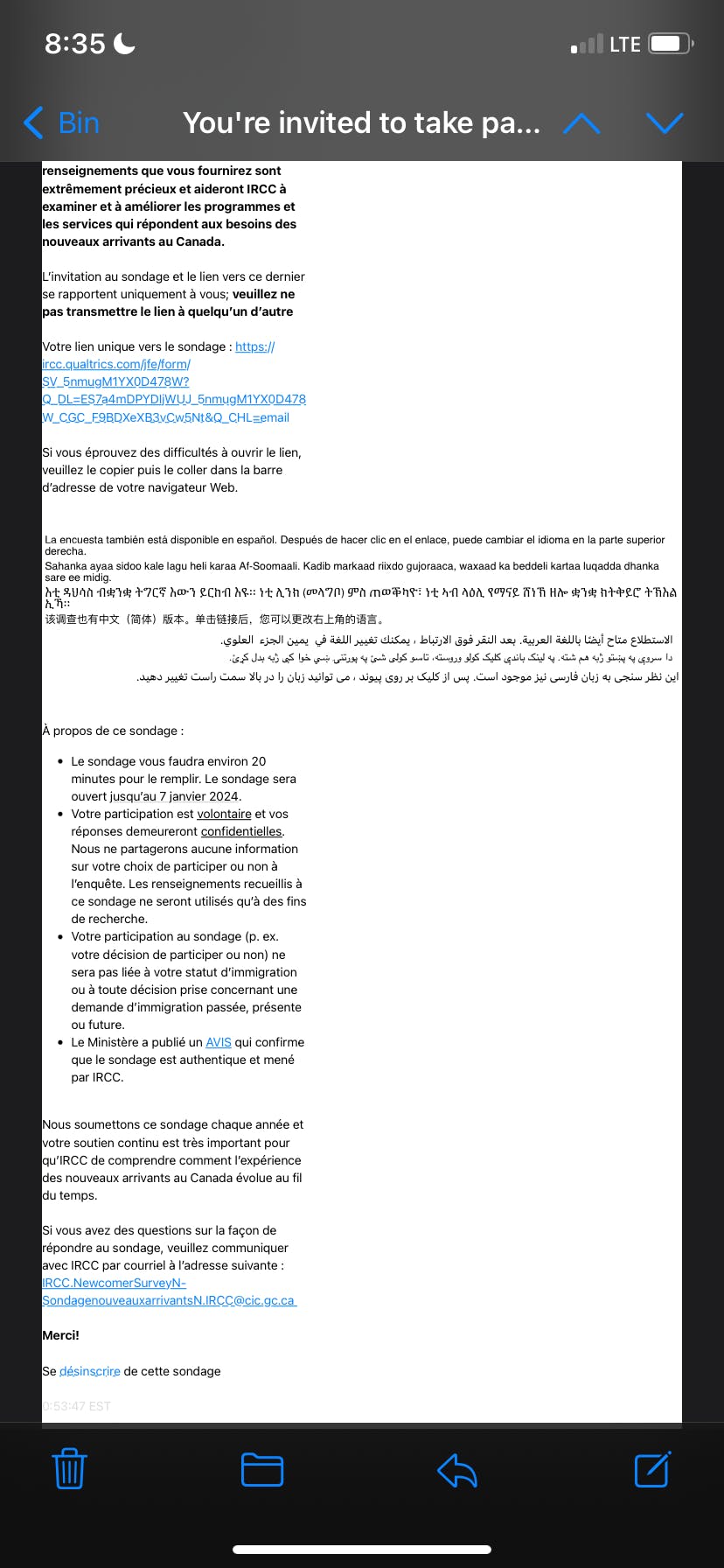
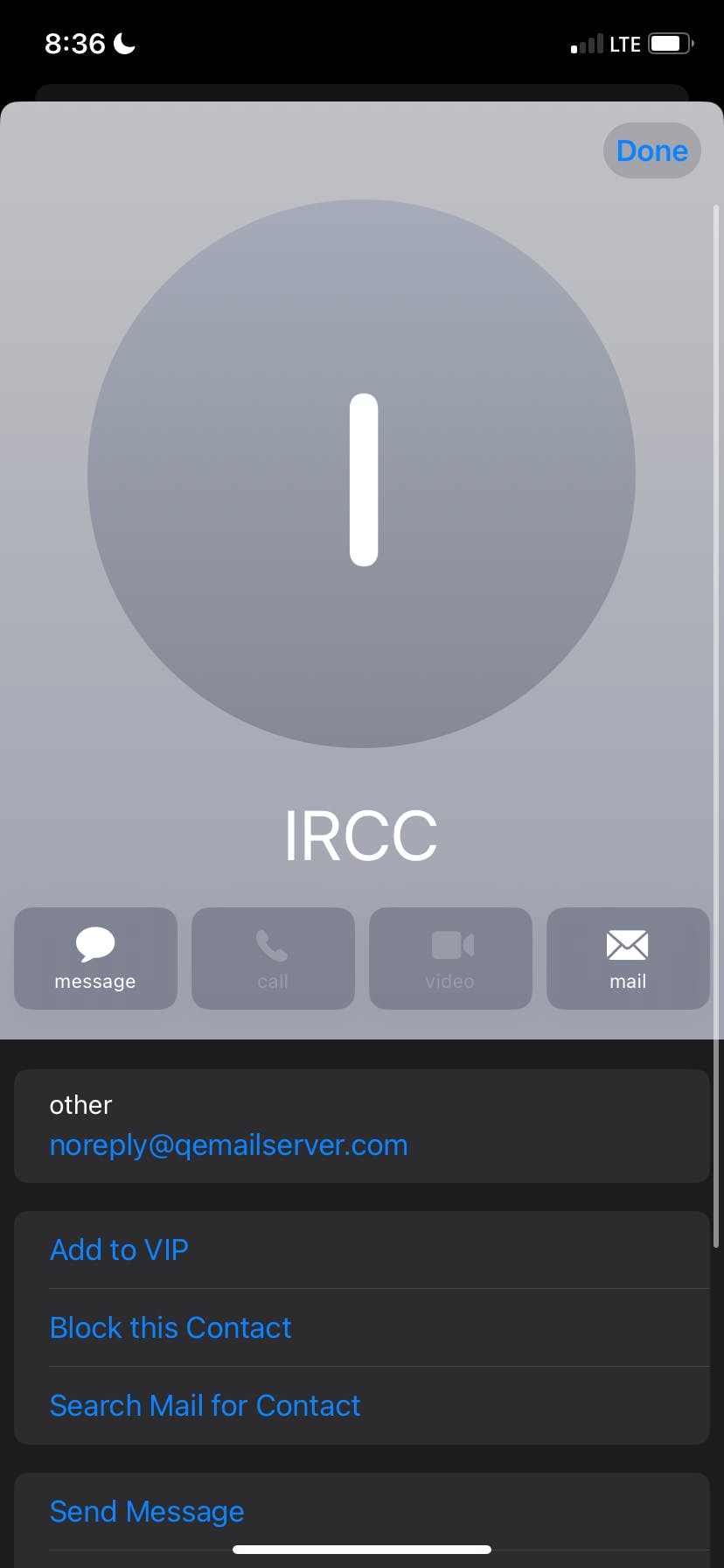
Not all phishing is easy to detect. But as you can see from this image, there are a lot of fishy signs in this email. First of all, this email is from IRCC, which means Black Hat is trying to make you feel urgent when you see it. They also make sure to write a brief message in the subject line. In the content, we can see that the text is not well aligned and is also multilingual. Legitimate communications from reputable organizations are typically well-written and professionally presented. You will also notice the URL that you want the black hat to click on. You think it's a safe website, but you're redirected to a malicious website that can steal your passwords or even install malware on your computer. You can also notice that the email "noreplyqemailserver.com" has nothing to do with IRCC even if it is hard to find out. Plenty of places let people rent an email server at a very low cost so they can use many types of email that look professional or authentic. Phishers often use addresses that resemble, but are not identical to, legitimate ones. Watch for misspellings or extra characters.
Securing Your Credentials:
Protecting your online credentials is paramount in the digital age. Implementing robust security measures ensures that your sensitive information remains safeguarded from potential threats. Companies can run simulated phishing campaigns as part of security awareness training. This provides employees with hands-on experience identifying phishing attempts and practicing the correct response. Here are recommendations to enhance the security of your online credentials:
Avoid using the same password across multiple accounts. If one account is compromised, using unique passwords prevents a security domino effect.
Craft passwords with a combination of uppercase and lowercase letters, numbers, and special characters. Avoid easily guessable information like birthdays or common words. For example, passwords containing qwerty, bonjour01 or 123456789 should not be used.
Activate 2FA whenever possible. This adds an extra layer of protection by requiring a secondary form of verification, such as a code sent to your mobile device, in addition to your password.
Change passwords periodically, especially for critical accounts. Regular updates mitigate the risk of prolonged exposure to potential threats.
Periodically review your account activity for any unauthorized access or suspicious transactions. Reporting discrepancies promptly enhances your ability to address potential security issues.
Keep your devices and software up to date with the latest security patches. Updates often address vulnerabilities that could be exploited by cyber threats.
Protection Tools:
Be wary of unsolicited messages. Most phishing attacks start with an email, text message or call that you didn't initiate. Be suspicious of any unexpected messages that ask for personal information.
Don't click on links in suspicious messages. Even if the message looks legitimate, avoid clicking on any links. Instead, type the URL yourself in the browser.
Avoid opening attachments. Phishing emails may contain malicious attachments that can install malware on your device.
Check the sender's email address. Hover over links to reveal the actual URL. Phishers often spoof legitimate email addresses.
Use a pop-up blocker. Some phishing attacks use pop-ups to trick victims into entering sensitive information.
Educate yourself. Stay informed about the latest phishing techniques and scams. Teach others about phishing prevention as well.
Report phishing emails. Forward suspicious messages to the relevant organizations to help combat phishing attacks.
Conclusion:
In conclusion, this article provides a comprehensive toolkit to arm yourself against phishing attacks. By following these practical tips, you will enhance your cybersecurity and contribute to creating a safer online space for everyone. Stay vigilant, stay informed, and navigate with confidence in the digital world.